Object Signing
Establish Trust with Ease
Creating a mutually authenticated network of devices, electronic documents, user identities, and other objects can be simple, quick, and cost-effective. VirtuCrypt’s technology is designed to be expansive enough to provide authentication for a wide variety of objects and versatile enough to integrate into your IT infrastructure with minimal configuration. This robust, turnkey, and easy-to-use solution enables your organization to implement the security of a public key infrastructure without the worry of high overhead or hardware requirements.
CA Security Measures
Ways organizations use certificate authority technology to enhance the security of their infrastructures:
- Signing sensitive files, such as electronic invoices
- Validating domains
- Authenticating individual users or subscribers
- Encrypting communication
- Securing e-mails
- Validating devices
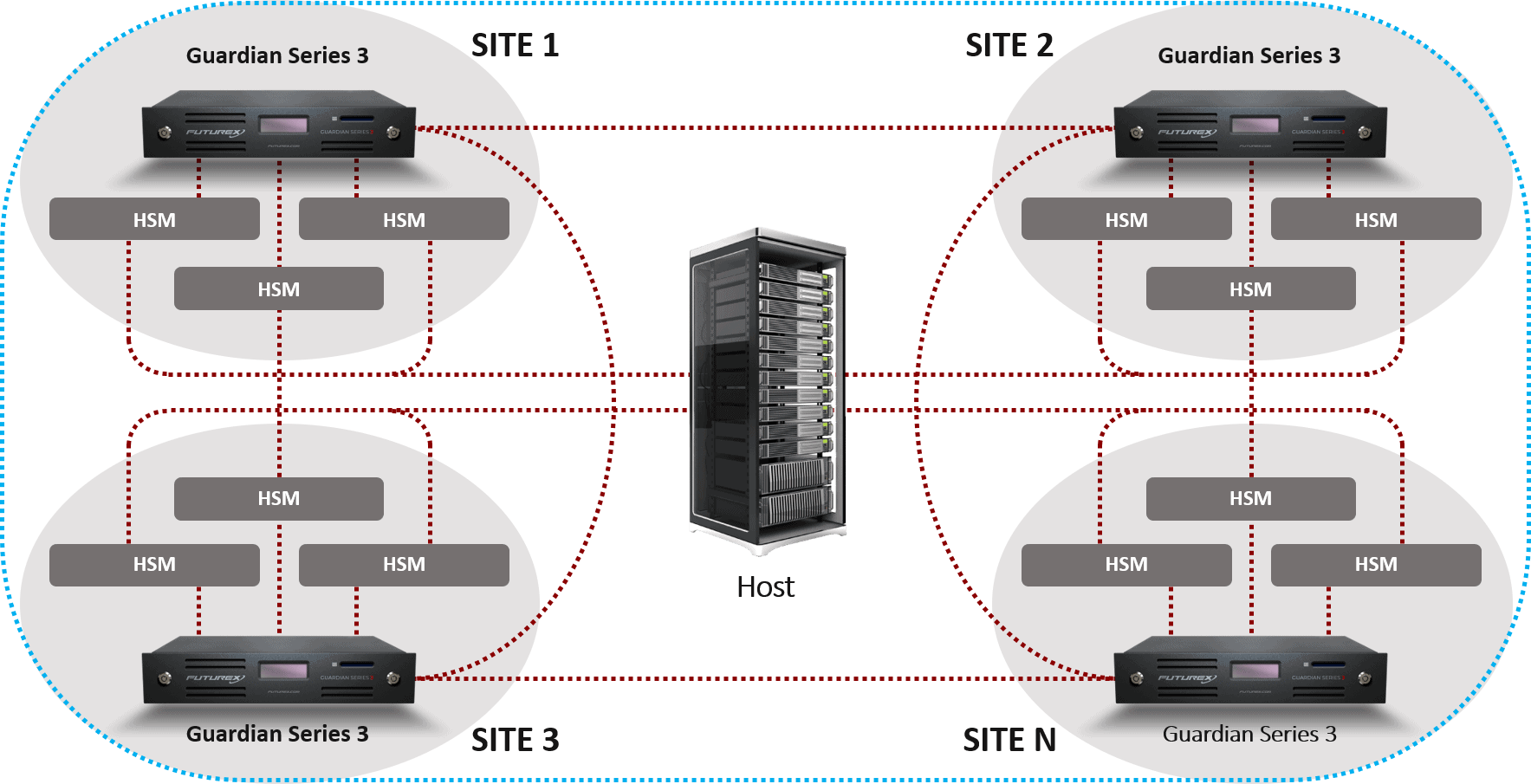
 How It Works
How It Works
VirtuCrypt’s Object Signing functionality enables individual objects to be validated by creating and storing asymmetric key pairs for the encryption, decryption, signature, and validation of data that relies on a public key infrastructure (PKI). VirtuCrypt handles the entire signing process, from creation of a self-signed root certificate and management of the subordinate certificate tree and asymmetric key pairs to management of Certificate Revocation Lists and devices. The VirtuCrypt Object Signing managed cloud services includes a validity period of up to 15 years for signatures.
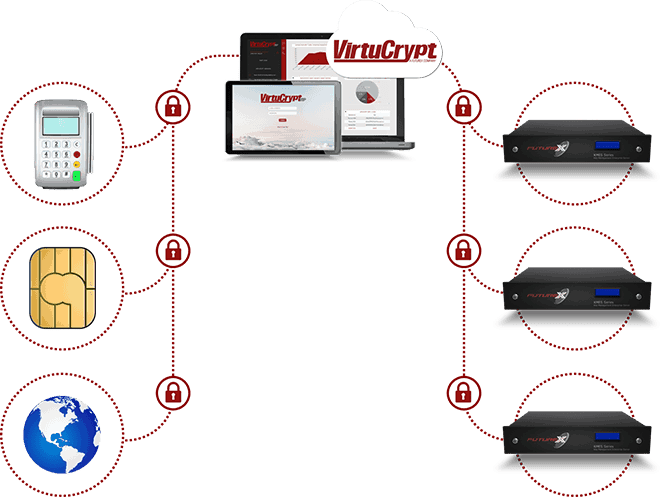
About PKI
A public key infrastructure (PKI) is the architecture through which two entities establish a trusted connection using asymmetric key pairs (public and private keys) for encrypting, decrypting, signing, and validating exchanged data. The connection could be between a host application and a linked device or simply between two users sharing an electronic document. This trusted connection, called mutual authentication, occurs when both objects are signed using a trusted certificate authority. Using certificates, each object is able to verify the other object’s authenticity, establishing a circle of trust.
Combining Services
VirtuCrypt Object Signing works best when paired with other VirtuCrypt Services. Point-to-Point Encryption, Remote Key Management, Debit Processing, and more are all available through VirtuCrypt on a per-use basis. Combining multiple VirtuCrypt makes for a more advanced cryptographic infrastructure. In general, VirtuCrypt’s offerings range from options for total custom cryptographic infrastructures to monitoring and alerting services. Interested in ensuring your infrastructure is secure in the event of a disaster?