Code Signing
Streamlined Support for Protecting Code
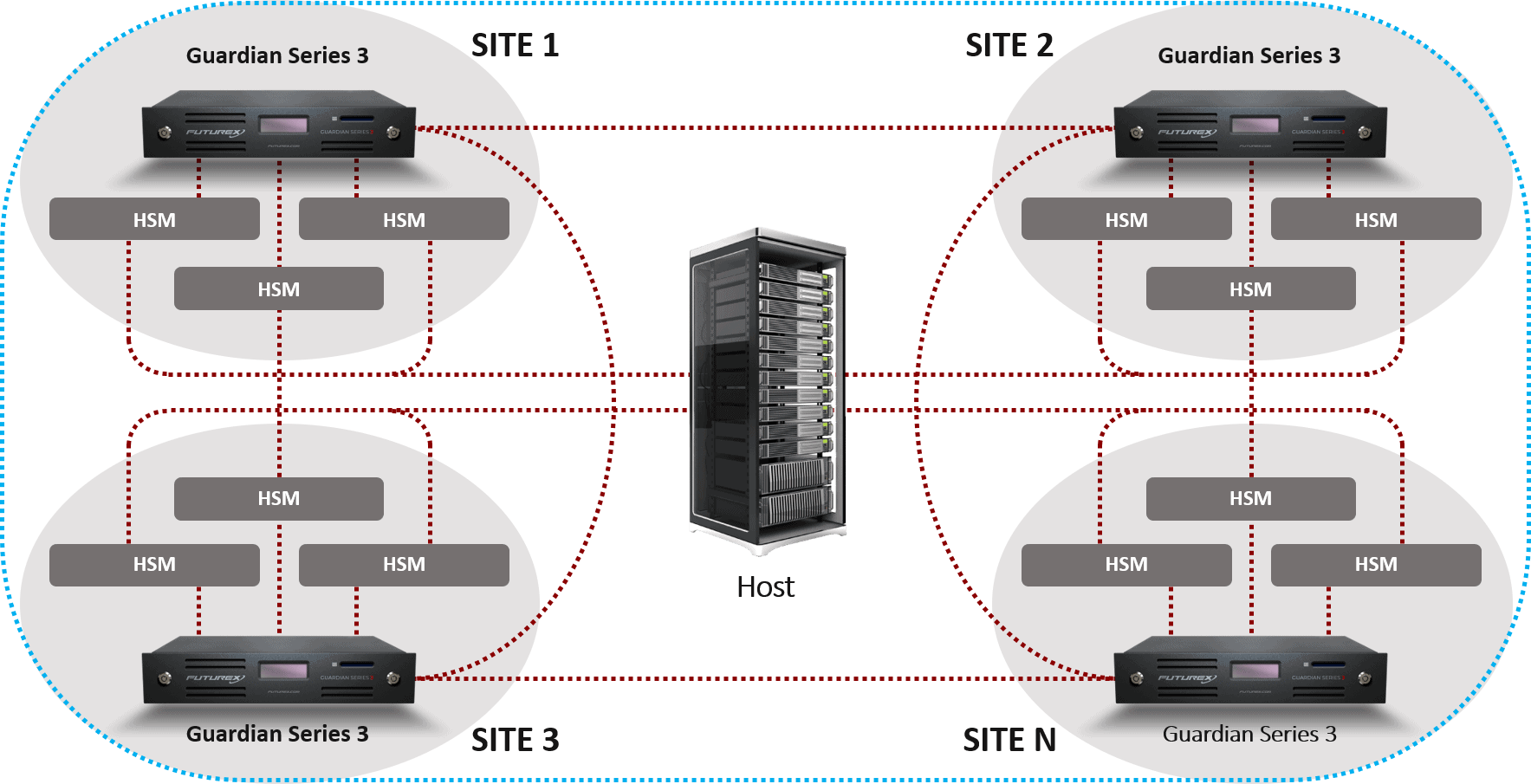
VirtuCrypt Code Signing provides protection for intellectual property, such as executables, by using a hardware security module (HSM) to secure a public key infrastructure (PKI). PKI is used to generate a digital signature, from which trust can be established.
Control and Prevent Threats
Code Signing deploys the following measures to ensure data is protected:
- Secures the process of signing code with an industry-compliant HSM
- Prevents and detects code tampering or counterfeit code
- Minimizes the possibility of external or internal attacks
 How It Works
How It Works
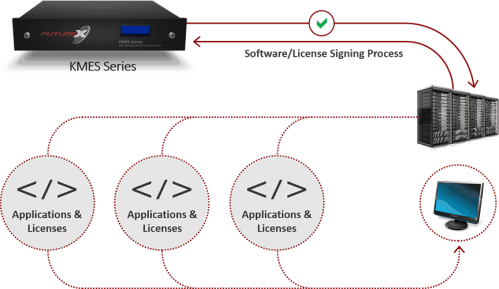
- Using PKI, both parties generate cryptographic key pairs.
- The code developer uses its private key to generate a digital signature for the code file. The developer sends both the digital signature and the code file to the recipient.
- The recipient combines the certificate, code file, and the developer’s public key to verify the identity and authenticity of the file.
If the developer’s private keys were stored on the server or in the clear, however, the threat of vulnerable private keys is introduced. Should private keys be intercepted, the party that obtains the private key can plagiarize the developer’s identity and publish code that appears to be authentic. This tarnishes the reputation of the developer and decreases their opportunities for business development. To prevent the negative consequences of unauthorized access of private keys, an HSM can be utilized to generate and store the keys securely.
Conserves Time and Resources
- All controls relating to VirtuCrypt services are managed using an intuitive web portal
- Creates a smooth process and workflow surrounding signing code
Protects Brand Reputation
- Prevents loss of revenue due to software counterfeiting
- Creates a reputation of trust with users of your organization’s software