Resource Library
Sales Brochures
VirtuCrypt-About Us
VirtuCrypt-About Us VirtuCrypt is Futurex’s enterprise cryptographic cloud platform. With VirtuCrypt, users can deploy FIPS 140-2 Level 3 validated cloud
VirtuCrypt Brochure-Cloud Payment HSM
VirtuCrypt Brochure-Cloud Payment HSM VirtuCrypt’s next-generation cloud payment HSM services give organizations a secure, compliant way to quickly deploy enterprise-grade
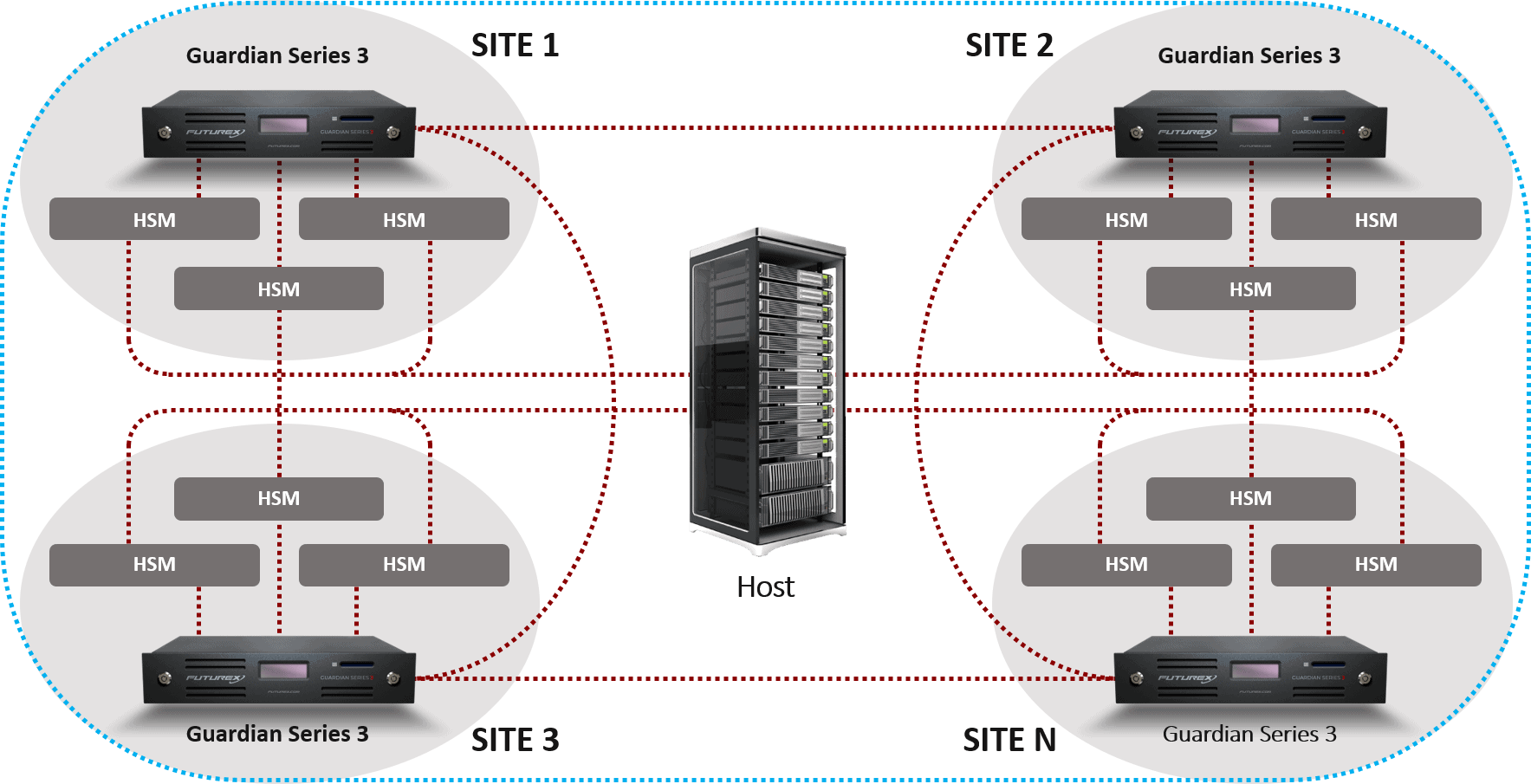
RKL with the KMES Series 3
RKL with the KMES Series 3 Remote key loading (RKL) is an indispensable tool for organizations in charge of ATMs,
Google EKM Integration
Google EKM Integration Google Cloud External Key Manager (EKM) allows you to create, store, and manage keys in a separate
Futurex CPoC 360 Service Brochure
Futurex CPoC 360 Service Brochure CPoC is a compliance standard developed by the PCI Security Standards Council. It stands for
Case Studies
Case Study Turnkey Migration to the Futurex Platform
Case Study Turnkey Migration to the Futurex Platform One of Africa’s largest independent ATM deployers and operators contacted Futurex seeking
CSU Case Study
CSU Case Study In 2021, the Brazilian payments organization CSU sought to pioneer banking as a service (BaaS). But their
VirtuCrypt Case Study Miura Systems
VirtuCrypt Case Study Miura Systems Miura Systems worked with VirtuCrypt to design and deploy a cloud-based remote key loading service.