CA & PKI
Simple Certificate and Key Management
Establishing a Public Key Infrastructure does not have to cost significant time, money, or work. Let VirtuCrypt supply you with an easy to use solution for managing all aspects of the certificate and encryption key lifecycle.
 What Is PKI?
What Is PKI?
A Public Key Infrastructure is formed by using certificates to ensure trusted, mutually authenticated communication.
- PKI certificates enable data objects and devices to prove their identity
- Private and public keys are used to perform a variety of encryption tasks, in a secure and compliant manner, on the data being exchanged
Applications
Using this versatile service, organizations can authenticate individual devices, programs, files, and more. VirtuCrypt’s certificate authority solutions can manage the entirety of all PKI processes, from creation of self-signed root certificates and management of the subordinate certificate trees and asymmetric key pairs to management of Certificate Revocation Lists (CRLs). Examples of the scope of CA solutions include, but are not limited to:
- File signing
- Domain validation
- User/subscriber authentication
- Encrypted communication
- Secure email
- Device validation
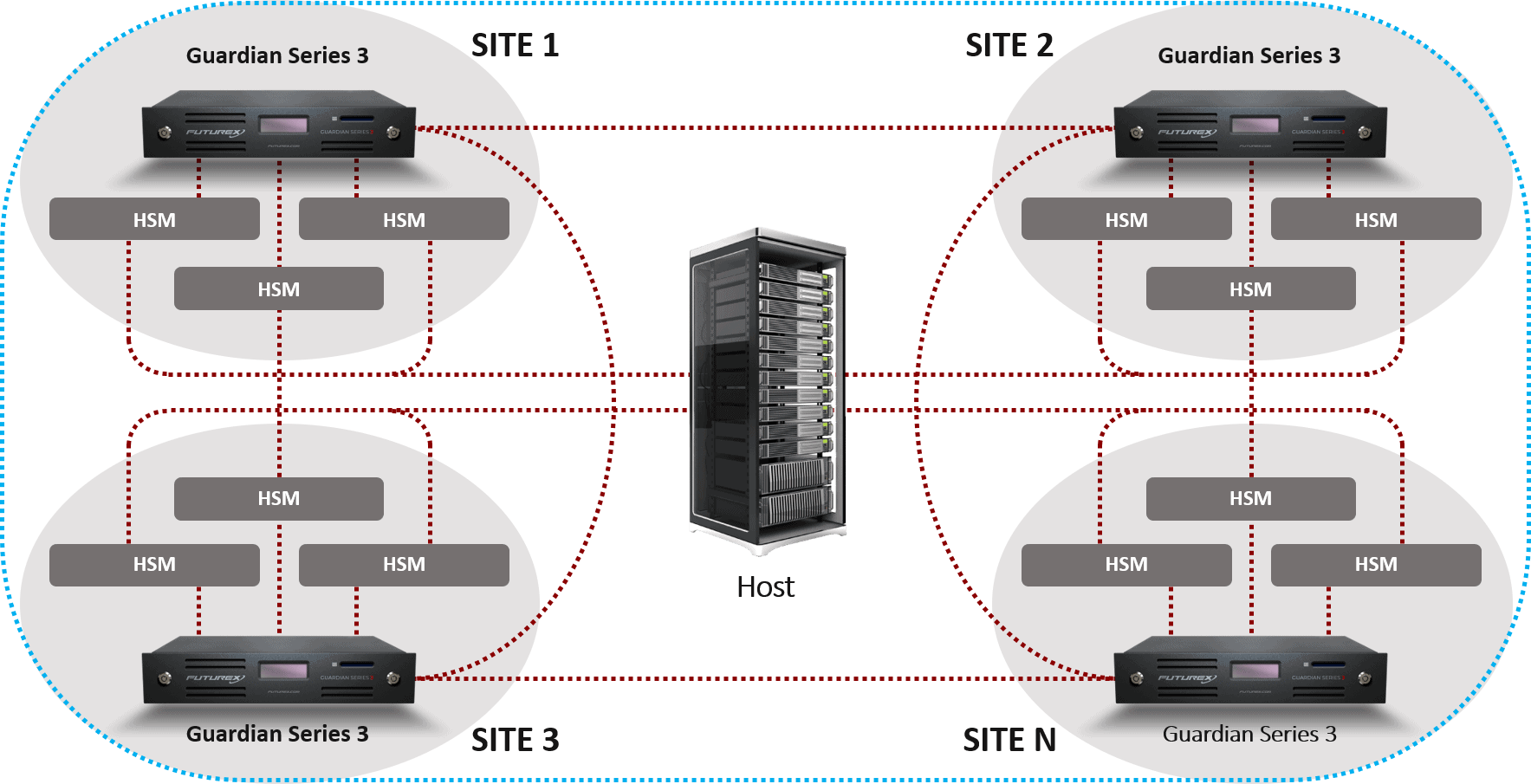
Communication Among Devices
Within the VirtuCrypt cloud, devices can be mutually authenticated to ensure all communication is secure and trusted, both to other Hardened Enterprise Security Platform solutions as well as to external host applications and client devices.
Security
VirtuCrypt incorporates FIPS 140-2 Level 3-validated Secure Cryptographic Devices (SCDs) into the key generation and loading process, providing dependable security. This service stores all required tracking and identifying information, allowing easy traceability for auditing requirements, and is compliant with all the required ISO, ANSI, FIPS, and PCI DSS regulatory requirements.